Guides/Monitoring network traffic from an Android app
To monitor and view network traffic in an Android application, you can use a proxy server. This guide will help set up your device and view network traffic from a specific Android app.
Prerequisites
To follow this guide, you have to have:
- an Android device (you do not need root access),
- a computer (with any operating system),
- a USB cable to connect your mobile device to the computer.
- access to a Wi-Fi network that you can connect to with the computer and the mobile device.
Install a proxy server
In this guide, we will use the Charles proxy server. There may be other, better alternatives that I have not tried using. Feel free to edit this guide if you feel like you have a better proxy server.
Note: The free trial version of Charles only allows for 30-minute sessions. After that time passes, you can reopen Charles to continue using it.
- Go to https://www.charlesproxy.com/download/ on your computer, and download the version of Charles for your operating system.
- Launch Charles.
- At the top bar, select the option Help > SSL Proxying > Install Charles Root Certificate on a Mobile Device or Remote Browser.
This will show a message box with your computer's local IP address and a port. In the next step, we will use this information to connect the mobile device to the proxy server.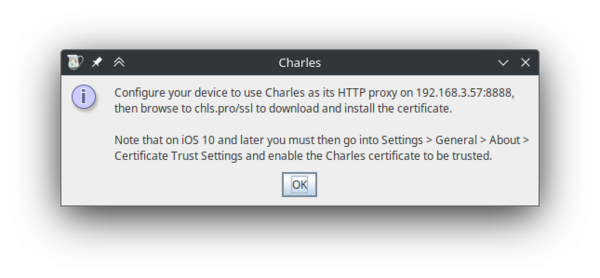
In this example, the IP shown on the pop-up is: 192.168.3.57, and the port is: 8888.
Set up proxy settings on the mobile device
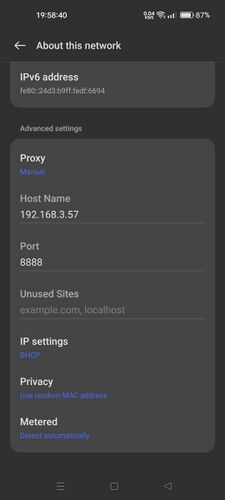
To make network traffic go from the device to your proxy server, you have to set proxy settings on your mobile device.
- On your mobile device, go to Settings > Wi-Fi and select your Wi-Fi network.
- Under Advanced settings, change Proxy to Manual.
- Set the Host Name and Port settings to the IP address and port displayed in the Charles pop-up window in step 1.
- Save the settings.
- If everything was done correctly, a pop-up should appear in Charles, informing of a new connection. Click on "Allow" to allow the proxy connection. If you click "Deny" on accident, you can simply restart Charles and try to connect to the proxy again.
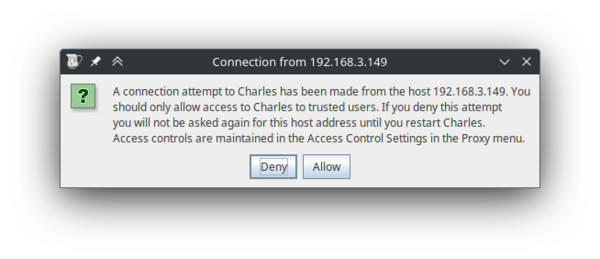
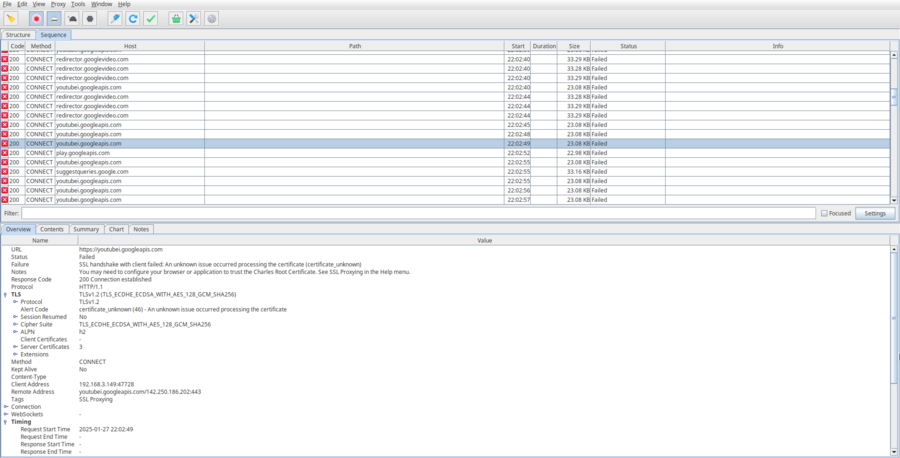
This pop-up window should appear on your computer after saving proxy settings on the mobile device. - After clicking allow, you can see some network traffic going through. You can try opening apps on your phone, and new entries will appear.
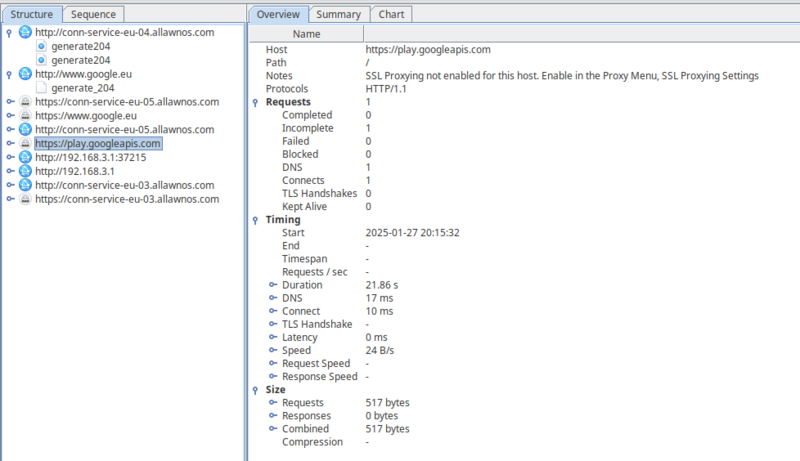
Network traffic from your mobile device, shown on your computer.
You can also enable Sequence view by clicking the Sequence tab on the top. This will show all of the network traffic in chronological order, with the most recent requests on the bottom.
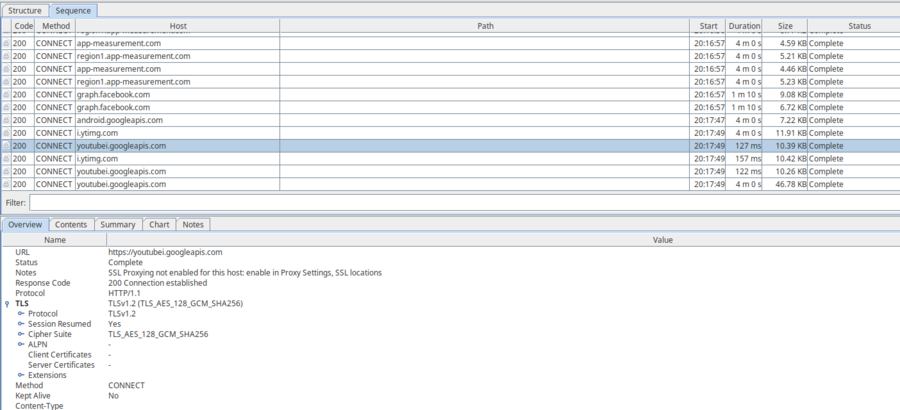
Now we have set-up our proxy server. However, even though we can see some host names and parts of requests, we cannot actually see the contents of most of the requests. This is because all modern applications use the HTTPS protocol to communicate; this protocol encrypts the data to prevent man-in-the-middle attacks.
This current setup will still work for HTTP requests. If you try to access a website via HTTP on the mobile device, you will be able to see the contents of the request, as well as the response in Charles. This is because, unlike HTTPS, HTTP is not encrypted, and the proxy server can read requests and responses sent via HTTP. You can try this yourself by opening an HTTP website (such as http://example.com/) in a web browser on your mobile device. You should see something similar to this:
(Note: You may need to scroll down to see the newest requests in Sequence view.)
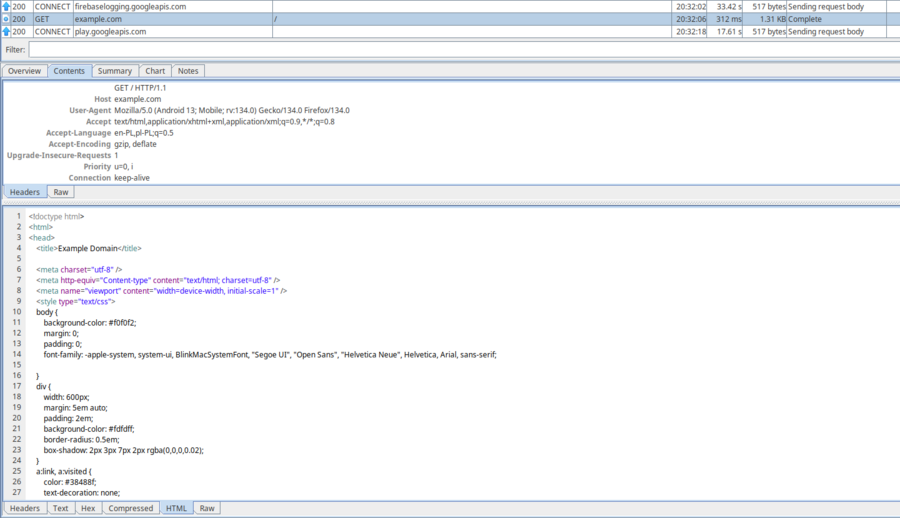
In the next steps, we will install a custom certificate and modify an application, which will allow us to intercept HTTPS requests as well.
Install a certificate to the mobile device
To look inside HTTPS requests, we need to install a certificate to our mobile device.
- On your mobile device, open your browser and type
chls.pro/sslinto the URL bar, while connected to the proxy. This will allow you to download the certificate for your instance of Charles. Tap on the "Download" button to confirm that you want to download the certificate file.
This URL is also shown in the Help pop-up window in Charles - it's in the same pop-up that we used to get the IP and port for the proxy settings. - Go to Settings and search for options about certificates. On my device, it is under Settings > Password & security > System security > Credential storage. From here, you should be able to view, add, and remove certificates installed on the system.
- Select Install certificates from storage, and then CA certificate.
- A pop-up may show up, warning you of the safety concerns related to adding custom certificates. Read it, and if you are sure you want to do this, tap on Install anyway.
Remember! After you are done exploring network traffic from an app, you can remove the certificate by going into this settings menu, selecting Trusted certificates, switching to the User tab, selecting the certificate and tapping on Uninstall. - You may be asked to verify your identity. After confirming your identity, you will be asked to choose a file. Select the file you downloaded before - it should be named
downloadfile.crtand it should be located in yourDownloadsfolder. - After selecting the file, the certificate should be installed. You can verify that, by going into the Trusted certificates menu, and selecting the User tab - your certificate should be there. You can tap on it to view detailed information about the certificate or uninstall it if you don't need it anymore.
The certificate should now be installed properly on the mobile device, however we still will not be able to see HTTPS traffic in Charles.
Enable SSL Proxying in Charles
To enable SSL proxying in Charles, do the following steps:
- From the menu bar at the top, select Proxy > SSL Proxying Settings....
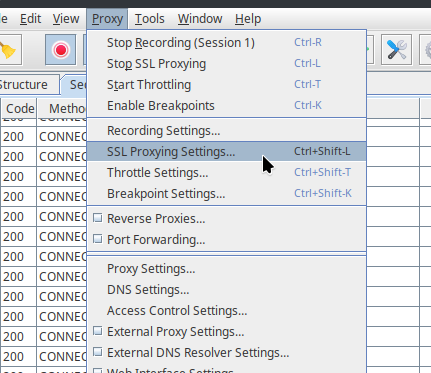
- Make sure the Enable SSL Proxying checkbox is enabled.
- Below the Include table, click on Add.
- In the pop-up, for the Host field, enter
*and leave the Port field empty. This will make it so all hosts' HTTPS requests will be captured and attempted to be read by Charles. - Click on OK on the pop-up, and OK on the "SSL Proxying Settings" window.
If you now try to open an application on your mobile device, you will see that it will not be able to connect to the servers. This is because all traffic is now captured by Charles. Most apps do not accept user-installed certificates as valid, which means even though our certificate is installed, the applications are acting as if it is an unknown certificate, and therefore cannot connect to the server at all.
If you want to allow some hostnames to use SSL as normal, you can add them to the Exclude table in the "SSL Proxying Settings" window. This setting makes it so Charles just acts as a pass-through for that specific host, and doesn't attempt to read any data inside of the requests. Alternatively, you can add hosts to the Include table instead of the * wildcard. This will make it so only the hosts in the Include table are captured by Charles.
Get APK files of the application that we will modify
We will modify the application slightly so that it will accept user-installed certificates. In this guide, we will be using Rizline as an example.
Install tools
First we will need to download some tools:
- To connect to the device via a USB cable, we will use Android Debug Bridge (adb)
- To decompile and build Android applications, we will use Apktool. To download and install Apktool, follow the instructions on this page: https://apktool.org/docs/install.
- To optimize the built APK, we will use zipalign.
- To sign the modified APK, we will use apksigner.
If everything is installed correctly, you should be able to open a terminal and type adb, apktool, zipalign and apksigner commands without errors.
Get APK files from the device
To modify the application files, we first need to get them onto our computer.
- Enable USB Debugging on your mobile device.
- To do that, go to Settings > Additional settings > Developer options > USB debugging (found in the Debugging section).
- If you cannot find the "Developer options" button, you might need to enable Developer Mode by going into Settings > About device > Version and tapping on the Build number option seven times. You should get a message saying "You are now a developer!"
- If you have any trouble with this, try following the official instructions from developer.android.com.
- Connect your Android device to your computer using a USB cable. Choose "Android Auto" on your device if prompted.
- On your mobile device, a pop-up should appear, asking for permission to allow USB debugging. Tap on allow; and if you plan on doing this often, you might want to tap the checkbox to always allow USB debugging from this computer. If the pop-up doesn't appear immediately, don't worry; it might appear after typing the command in the next step.
- On your computer, open up a terminal and type:
adb shell
You should now have access to your mobile device on your computer via the terminal.
*hacking noises* we're in. -
Now we need to find the package ID of the app that we are interested in. One way of doing that is finding the ID in the list of installed packages. In
adb, type the following command to show the list of packages installed on the device:pm list packages
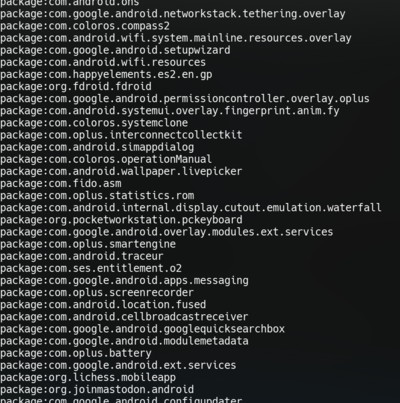
On my device, this command shows 443 packages. Here is a few of them. This command will only show the package IDs, so you cannot search by name. If you have a lot of applications installed, you might want to try piping the command to
grep.grepis a command line utility that will filter down results by showing only the lines that have a specified string of text inside of them. For example the following command will show applications that contain the word "Pigeon" in their ID:pm list packages | grep Pigeon
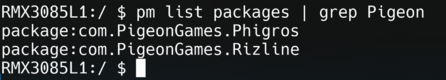
This time, only applications made by Pigeon Games will be shown.
Another way of getting the ID of an application, is just searching the app on the Google Play Store website. When you go to an application page on Google Play, the ID of the package will be embedded in the URL. For Rizline, the link is https://play.google.com/store/apps/details?id=com.PigeonGames.Rizline, and so the package ID iscom.PigeonGames.Rizline.
-
The next step is to find the path of the APK files on the mobile device. Note that it is common for one application to have multiple APK files. Usually, there is one
base.apkfile, that is common for all devices, and severalsplitAPK files, that are device specific. For example, if your mobile device has a larger screen, it may download asplitapk with extra high-quality assets. To find the paths to the APK files, you can use thepm path <package_id>command. In our case, the command will be:pm path com.PigeonGames.Rizline
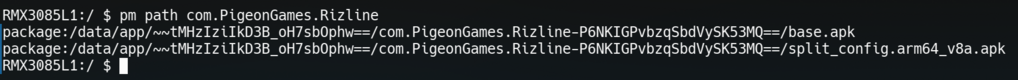
Rizline has two APK files - a base.apkfile and asplit_config.arm64_v8a.apkfile.Now we know that the paths to our two APK files are:
/data/app/~~tMHzIziIkD3B_oH7sbOphw==/com.PigeonGames.Rizline-P6NKIGPvbzqSbdVySK53MQ==/base.apk, and/data/app/~~tMHzIziIkD3B_oH7sbOphw==/com.PigeonGames.Rizline-P6NKIGPvbzqSbdVySK53MQ==/split_config.arm64_v8a.apk. We can use that information to download the files from the device to our computer.
-
Exit the
adb shell:exit
-
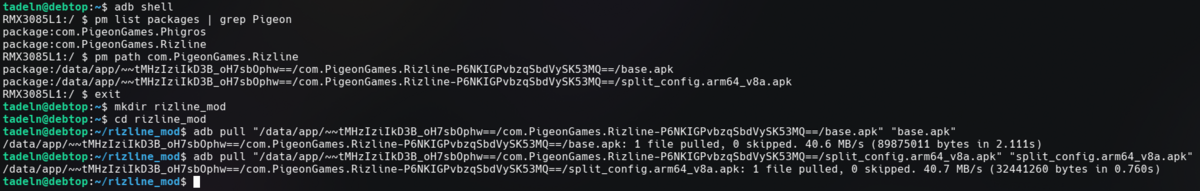
Create a new directory for our APK files. To do that, you can either create it using a GUI file explorer, or by typing the
mkdircommand. In my case, the directory name isrizline_modmkdir rizline_mod
-
Navigate to the new directory using the
cdcommand.cd rizline_mod
-
Now we can use the
adb pullcommand to copy the files to the computer.adb pull "/data/app/~~tMHzIziIkD3B_oH7sbOphw==/com.PigeonGames.Rizline-P6NKIGPvbzqSbdVySK53MQ==/base.apk" "base.apk" adb pull "/data/app/~~tMHzIziIkD3B_oH7sbOphw==/com.PigeonGames.Rizline-P6NKIGPvbzqSbdVySK53MQ==/split_config.arm64_v8a.apk" "split_config.arm64_v8a.apk"
The
adb pullcommand takes two arguments: the first one is the path on the mobile device, and the second one is the destination path, on your computer. In this case, we just name the resulting filesbase.apkandsplit_config.arm64_v8a.apkrespectively.
Modify an application to allow user-installed certificates
To modify the files of an APK package, we will first need to extract individual files from the downloaded APK files.
APK files are essentially just ZIP files in disguise. If you change the .apk file extension to .zip, you can open the file in any archiving software, just like a normal ZIP file. However, some files inside the APK file (such as AndroidManifest.xml) are in a weird, binary format. To read all of the files properly, we will use Apktool.
Decompile the APK files using apktool
- Open a terminal in the directory with your copied APK files.
-
Type the following commands to decompile the APK files using Apktool:
apktool d base.apk apktool d split_config.arm64_v8a.apk
This will create new directories -
baseandsplit_config.arm64_v8awith the contents of the APK files.
You can now explore the application files freely using a file manager.
Add a new file: network_security_config.xml
The first change we will make is adding a new file in base/res/xml/network_security_config.xml with the following contents:
<network-security-config>
<debug-overrides>
<trust-anchors>
<!-- Trust user added CAs while debuggable only -->
<certificates src="user" />
</trust-anchors>
</debug-overrides>
</network-security-config>
This file will allow the app to trust user-added certificate authorities.
Change the AndroidManifest.xml file
Change the application name
Build and sign the modified APK
Install the modified APK to the device
This page has some work to do. Help the wiki by editing this page!
- Add download link to adb, zipalign and apksigner
- Finish the guide